Proxy authentication is a process that enables users to establish verification methods for their requests before processing.
According to Statista, 26% of global online users utilized proxy servers to access web content in the first quarter of 2018, with expectations for further growth in the coming years.
Users can validate proxy access by providing specific credentials, ensuring that only authorized users gain entry. This article will guide you by outlining the two ways for proxy authentication.
What is Proxy Authentication?
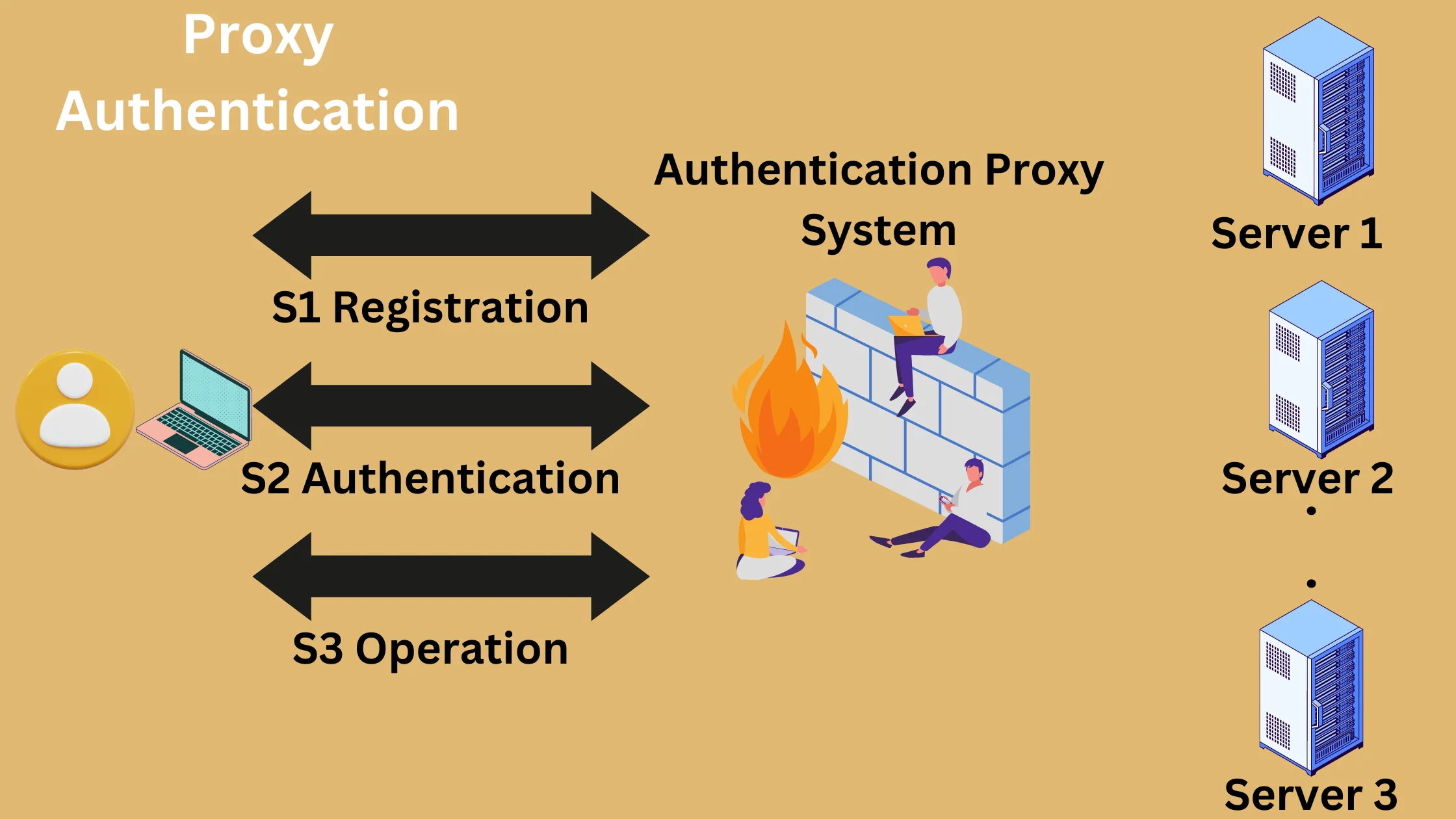
Proxy authentication allows you to set up how the proxy server works, checks and confirms the identity of client machines trying to access proxies.
Normally, the proxy authentication feature is turned off, and you need to enable it if you want to make new rules for users or groups.
How Does Proxy Authentication Work?
Proxy authentication is a security process that checks and confirms a client’s request. Proxies act as access controllers, allowing or denying requests based on whether the user provides valid credentials for access.
The HTTP proxy-authenticate header specifies the authentication method needed to obtain access permission from the proxy server.
Clients that communicate with proxies send HTTP requests that include information about their requests and clients in the request header field.
The proxy server responds by requesting credentials for verification through the HTTP response message.
Proxies authenticate users by validating their identity with appropriate credentials in order to ensure only authorized users are allowed to access proxy servers.
Two Methods of Proxy Authentication
Proxy authentication can happen in two ways. The first method involves using a username and password, while the second method uses an IP address for authentication.
When you sign up with a proxy provider, they give you a username and password along with a set of proxies. After purchasing the proxy package, you need to set up your username and password.
Once the payment process is complete, you’ll receive a confirmation email containing the list of proxies. This ensures that only authorized users with the correct credentials or IP addresses can access the proxies provided by the service.
1. Proxy Authentication via Username & Password

To access residential proxies, users need to log in using a username and password.
They create these credentials using basic authentication and then include them in the HTTP request within the Proxy-Authentication header. These credentials serve as the key to accessing all proxies in their pool.
For better security, unique credentials are assigned to each individual proxy. This is particularly effective for residential proxies that offer access to location-specific proxies.
Proxies are provided via email, including the IP address and port number. The username and password are crucial for authenticating and accessing these proxies.
2. Proxy Authentication using IP address

The most secure way to authenticate is by using an IP address. When you choose IP authentication, you need to set up the IP and port in your proxy settings.
Configure your browser to use the IP address you’re scraping, and it’s advisable to include this IP address in the proxy provider’s dashboard or via their service API.
This process, known as whitelisting, means you’re pre-approving your IP address with the best proxy provider, allowing you to access proxies without needing a username or password.
By using your whitelisted IP address instead of proxy authentication headers, you gain access to the proxies without having to send proxy authentication headers.
This makes tasks like HTTPS requests with web browsers or testing with Selenium easier since there’s no need for a proxy authentication header.
HTTP Proxy-Authenticate Message
The Proxy-Authenticate header is essential for accessing files and folders from the server, especially when users request confidential information.
When the server needs the user’s credentials, it responds with an HTTP status code of “407,” indicating that “Proxy-Authentication is Required.”
This message (HTTP 407) is a response from the server to the client, and it serves as an authorization method for the server to validate the client when a proxy is requested.
An authorization credential is not present on the server, so this message will be returned when the server is unable to fulfill the request. In response, the client provides the requested credentials, and after validation, the server fulfills the client’s requests.
HTTP 407 Response Message
When a user wants to use proxies to scrape a website, the proxy server responds with a 407 status code, asking for access credentials.
The user gets this message and collects the needed credentials, either from a local database or by asking the user directly.
After gathering the credentials, the user sends the HTTP request again, but this time includes the credentials in a proxy-authorization header field.
Using valid credentials, the user can access the proxy servers. Otherwise, another 407 request is sent.
An HTTP proxy-authenticate header can be thought of as a password for ensuring the user is allowed to access a proxy server.
Syntax
Proxy-Authenticate:<type>realm=<realm>
There are other types of checks besides security checks identified by the Internet Assigned Numbers Authority (IANA). The most common one is Basic, where a user provides a username and password to prove who they are.
On the other hand, “<realm>” tells us about the protected area, which is often a website that the user is trying to get into. It’s like a specific zone that needs the user to prove their identity before allowing access.
Quick Links:
- The Risks of Not Hiding Your IP Address
- Role of Proxies in Online Security
- Reasons To Hide Your IP Address
- How to Test Proxies?
Final Thoughts
To sum it up, when we compare different ways of proving you’re allowed to use a proxy, we see that proxies are important for checking if users are legitimate and keeping online activities safe.
There are two main ways to prove you’re allowed to use a proxy: by providing a username and password (called Basic authentication) or by confirming your IP address (known as IP authentication).
Basic authentication is easy for users but may not be as secure. IP authentication is more secure as it only allows certain IP addresses, making it harder for unauthorized users to get in.
The best choice depends on what the user needs, how secure they want to be, and what type of proxies they are using.
Understanding these methods helps users make smart choices based on their specific situations and preferences.
FAQs
What are the common methods of proxy authentication? 🤔
The most common methods for proxy authentication include: Basic Authentication: Uses a username and password for authentication but sends information in clear text. Digest Authentication: Similar to basic authentication but with added security features, where credentials are sent encrypted. NTLM (Windows NT LAN Manager): A challenge-response authentication protocol used in Windows networks. Kerberos: A more secure method that uses tickets to authenticate a user without transmitting passwords. OAuth: A token-based authentication used for API access in various web services. Certificate-Based Authentication: Uses digital certificates to authenticate users, providing a high level of security.
How do I set up proxy authentication? 🛠️
Setting up proxy authentication typically involves configuring your proxy server settings to require authentication and then specifying the authentication method you wish to use. The exact steps can vary depending on the proxy server software you're using, so it's important to consult the documentation for your specific proxy solution.
Can I bypass proxy authentication? 🚫
Bypassing proxy authentication undermines security protocols and is not recommended. It can expose networks to unauthorized access and potential security threats. Instead, if you're facing issues with proxy authentication, it's better to consult with your network administrator to address the problem legitimately.
How do I troubleshoot proxy authentication issues? 🛠️🔍
If you're experiencing proxy authentication issues, consider the following steps: Check Credentials: Ensure you're using the correct username and password. Review Proxy Settings: Verify that your proxy settings are configured correctly. Update Software: Make sure your proxy server and client software are up to date. Consult Logs: Check the proxy server logs for any error messages that can provide clues. Contact Support: If you're still having trouble, reach out to your proxy server's support team for help.
