If you’ve received a message saying your IP address is flagged as an open proxy, it might sound confusing. Don’t worry; I am here to simplify things.
An open proxy is a tool that adds a layer of privacy to your online browsing, but it can have downsides. If your IP address is flagged, it means there could be some issues.
In this guide, I’ll break down what open proxies are, how they function, the potential problems they pose, and why your IP might get wrongly tagged.
Understanding these aspects is crucial for securing your online activities. Let’s talk about the details and come up with a solution together.
What Is An Open Proxy?
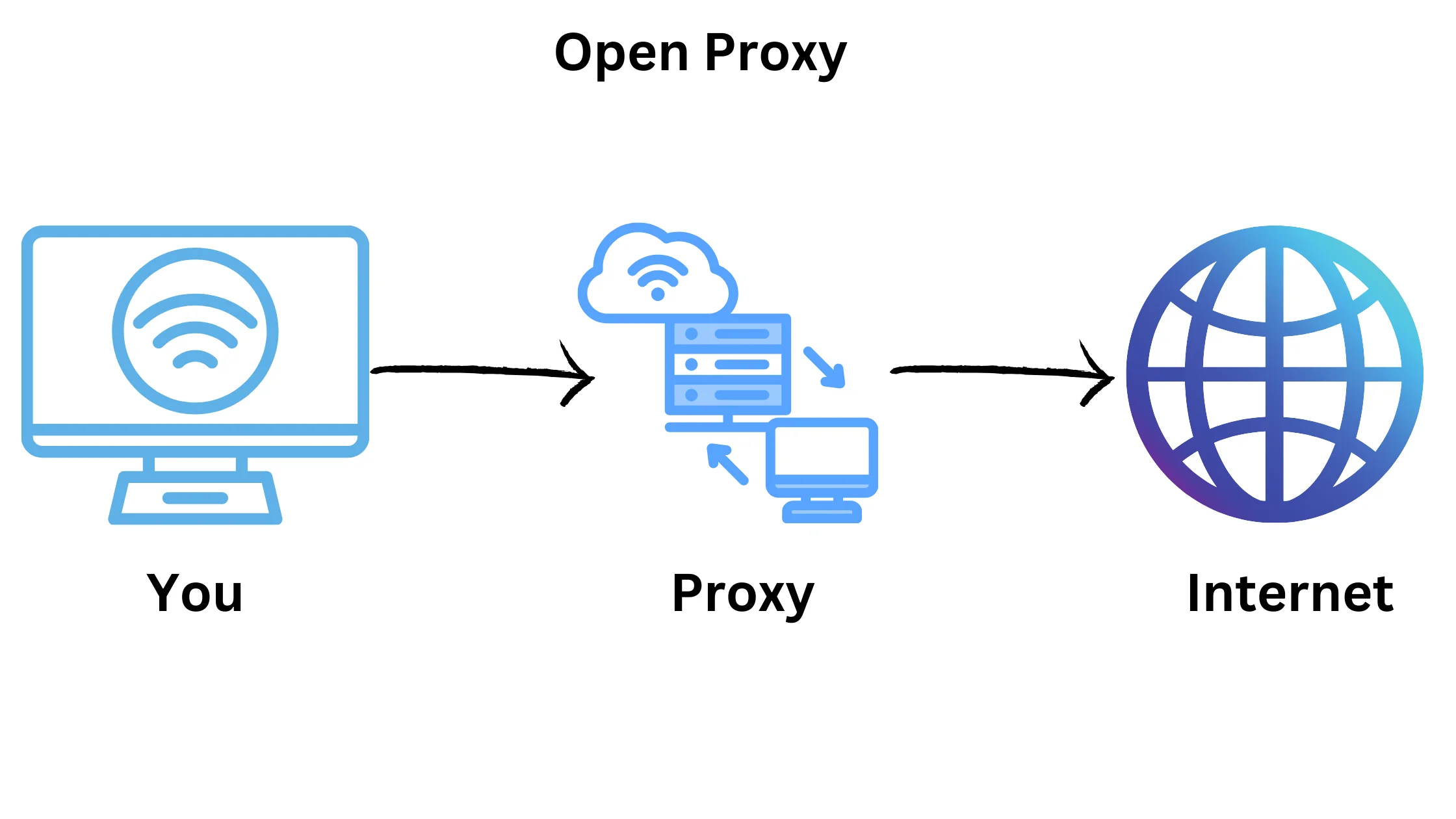
An open proxy is like a helper on the internet that lets you browse websites without directly showing your location.
It works by standing between your computer and the websites you visit, forwarding your requests, and bringing back the responses.
Anyone can use open proxies without needing permission, but there are risks involved, so it’s essential to be cautious when using them.
What Are the Advantages Of An Open Proxy?

Using an open proxy server helps you browse the internet more privately. It works by sending your internet traffic through another server so the websites you visit see the proxy server’s IP address instead of yours.
This can be handy to access content from your home country while abroad and get around content restrictions. It also makes it harder for others to track your online activities.
However, using a proxy may not be allowed by your internet provider, so it comes with some risks.
What Are The Risks of Using An Open Proxy?
While open proxies may boost your online privacy, they come with risks. These servers, open to the public, treat all traffic the same, allowing both good and bad data.
Cybercriminals exploit this to target victims, launch attacks and spread spam or viruses. Multiple users on open proxies can lead to slow internet and website issues.
Many networks and websites block traffic from open proxies due to their association with malicious activities, making it challenging to access some content.
ISPs proxies and administrators may also restrict traffic from known open proxies to prevent fraud and online threats.
Why Has Your IP Address Been Flagged As an Open Proxy?
Sometimes, your IP address might be labeled as an open proxy. Imagine you’re trying to use Instagram, and suddenly, you see a message saying your IP has been flagged as an open proxy.
This means Instagram has put restrictions on your IP. Similar issues can occur on other platforms, leading to what’s known as an IP ban. Several reasons can cause this:
- Server Misconfiguration: If you have a proxy server on your network, but it’s not set up correctly and allows unauthorized access, various online services and security software might think it’s an open proxy and block it.
- Malware or Botnet Infection: Your server or device could be acting like an open proxy if it’s infected with malware or part of a botnet infection. Cybercriminals might be using your device as a proxy for their harmful activities.
- Previous Misuse: If the IP address you’re using has a history of engaging in harmful online behavior, it could trigger a warning.
- Shared IP Address: If you’re on a shared proxy network like public Wi-Fi, sharing an IP address with others who use it for proxying traffic could lead to a flag.
- Suspicious Traffic Patterns: If your IP is generating a lot of traffic that looks like it’s from an open proxy, tools designed to detect such behavior might flag it.
How Do You Detect An Open Proxy?

Organizations use different techniques to find open proxies. Let’s break down the common methods:
- Port Scanning: Imagine a tool scanning a bunch of addresses to see if certain doors (ports) are open. If it finds ports linked to open proxies, it raises a flag.
- Traffic Behavior Analysis: Some systems keep an eye on how data moves through networks. If there’s a lot of traffic or too many connection requests, which are typical signs of proxy use, it alerts them.
- DNS Query Analysis: Think of DNS queries like asking for directions on the internet. If someone is asking for routes related to proxy services, it might trigger suspicion.
- Monitoring Access Logs: Just like keeping track of who enters a building, organizations watch logs for websites and networks. Unusual patterns, like one address making tons of requests, might indicate proxy activity.
- Blocklists: Organizations maintain lists of known open proxies and bad IP addresses. When they see an address behaving like a proxy, they check it against these lists.
- Community Reporting: Users and network experts report odd behaviors to organizations. This helps keep an eye on IPs showing proxy-like signs.
How Do You Know If Your IP Is An Open Proxy?
To make sure your online identity and network are safe, follow these simple steps to check if your IP is flagged as an open proxy:
- Online Proxy Checker: Think of this like using a tool to see if your house has any open doors. Online tools can quickly check if your IP is acting like an open proxy.
- Public IP Reputation Lists: Imagine there’s a neighborhood watch for IPs. Cybersecurity groups and internet service providers keep lists of IPs with a bad reputation. Check if your address is on these lists.
- Analyze Traffic Patterns: It’s like watching the flow of traffic on a street. If your IP is making an unusually high number of requests or showing behavior typical of a proxy, there might be a concern.
- Check Server and Proxy Settings: Think of your online setup, like setting up your house. Ensure your online tools are not mistakenly configured to act like an open proxy.
- Contact Your Internet Provider: If you think there’s been a mistake, talk to your Internet service provider. It’s like reporting an issue in your neighborhood. They can help clear your name if you’ve been wrongly flagged.
How To Disable Open Proxies?
If you’re using Chrome and want to stay secure by avoiding open proxies, follow these simple steps:
- Click on the three dots at the top-right corner of your browser. It’s like opening a menu.
- Go to “Settings.” Think of this as going into your browser’s control center.
- This is similar to entering the technical settings on your computer. In the “System” menu, select “Open your computer’s proxy settings.”
- You can disable an automatic system in the “Automatic proxy setup” section.
- In the “Manual proxy setup” section, turn off “Use a proxy server.” It’s like saying no to using a middleman.
- Click “Save” to keep these changes. It’s like confirming your choices.
An explanation of how to disable access to an open proxy server for Chrome users on Mac can be found here:
Sure, if you’re using a computer and want to make sure you’re not using any proxy settings, follow these steps:
- Click on the three dots at the top-right corner of your browser. Think of these dots like a menu button.

- Choose “Settings” from the menu. It’s like going into the control center of your browser.
- Look for “Systems” and select it. It’s a category in the settings menu.
- Click on “Open your computer’s proxy settings.” This is like opening a door to the more technical settings.
- Uncheck all the options under the “Proxies” tab. Using switches to turn off proxies would be like saying, “I don’t want any.”
- Select “OK” to save these settings. This is like confirming your decision
Quick Links:
- How To Configure A Proxy Server On iPhone and iPad?
- How to Configure a Proxy Server on Android?
- How Proxies Help Improve Ad Verification?
Conclusion
To stay safe from the risks associated with open proxies, it’s crucial to keep your IP address private and avoid sharing it. Connect to secure and private Wi-Fi networks, steering clear of public ones.
Review and secure your network settings, including your router and firewall, to prevent unauthorized access.
Ensure your Wi-Fi network is protected with a robust password and encryption for added security. If you remotely access network devices, implement strong authentication methods like Two-Factor Authentication (2FA).
Regularly monitor your network traffic for any unusual activity, especially a surge in connection requests. For enhanced privacy, consider using a reputable VPN service, which not only hides your IP address but also encrypts your online activity.
Taking a proactive approach to network security minimizes the risks associated with open proxies and reduces the likelihood of being mistakenly flagged as one.
